All Blogs
November 21, 2024
Critical Security Findings at the University of Cambridge: A Methodology for Detecting Exposed Credentials
How I discovered two critical vulnerabilities that exposed sensitive credentials and led to unauthorized access. b-ismi-llāhi r-raḥmāni r-raḥīmi — In…
November 20, 2024
Hacking Real-world AI Systems: The Art of Prompt Injection Attacks — Part 1
Ready to Hack AI models? Learn How to Hack AI Systems and Access Sensitive Data. Discover How Prompt Injection Can…
November 19, 2024
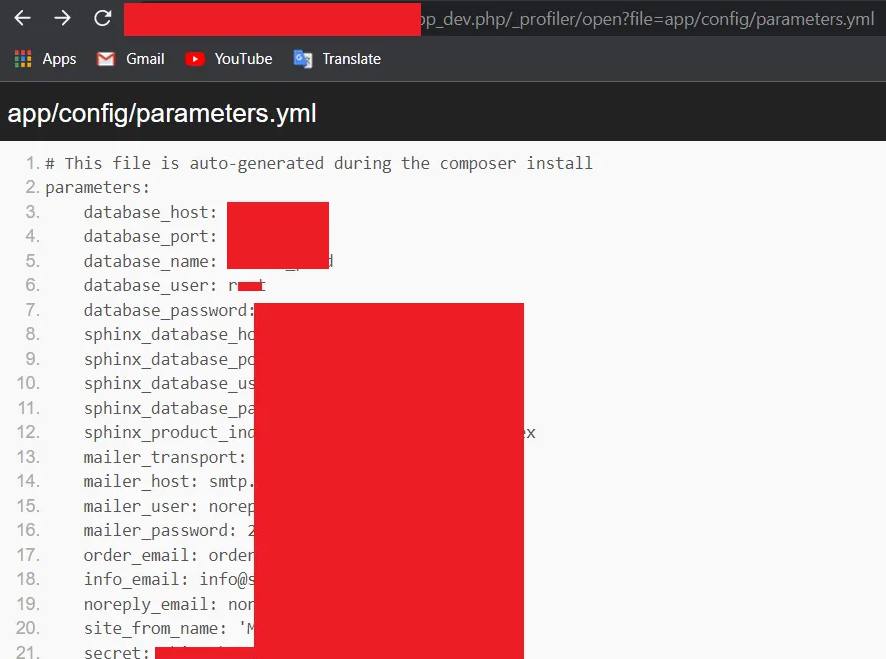
How I was able to find multiple vulnerabilities of a Symfony Web Framework web application
Found high severity vulnerability in 5 minutes just from reconnaissance. Found multiple vulnerabilities on a web application that used the…
November 6, 2024
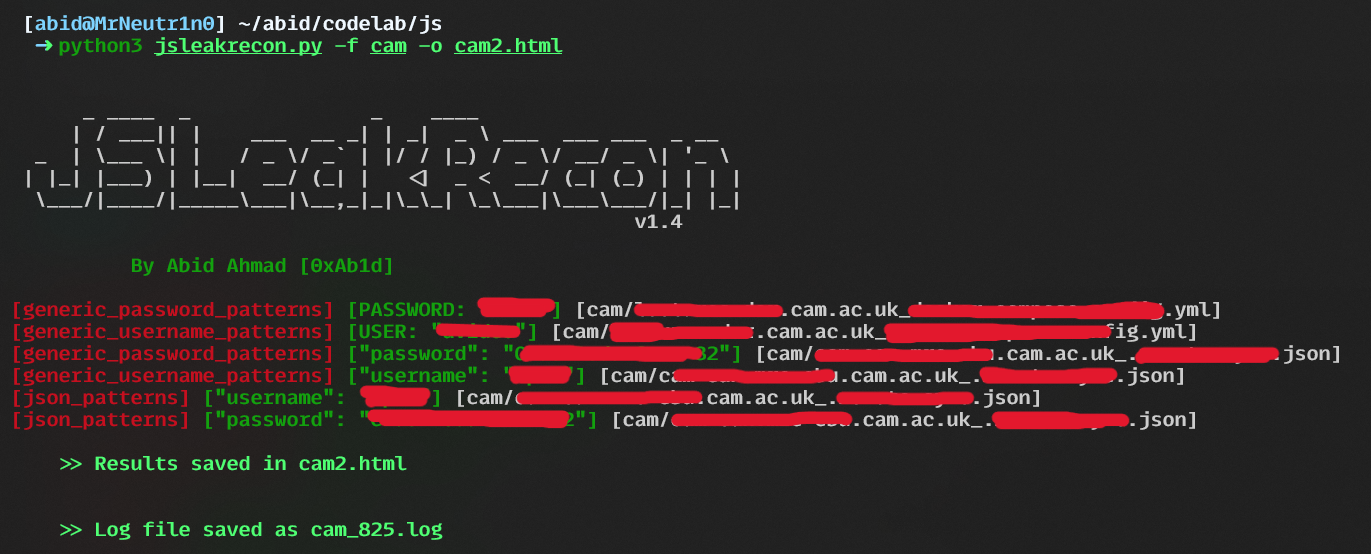
JSLeakRecon: The Ultimate Tool for Detecting Potential Leaks in JavaScript Files
Quickly Identify Hardcoded Credentials, API keys, Access Tokens, Secret keys, and Critical security issues in JavaScript Files b-ismi-llāhi r-raḥmāni r-raḥīmi…
All Categories
- Writeups (4)