JSLeakRecon: The Ultimate Tool for Detecting Potential Leaks in JavaScript Files
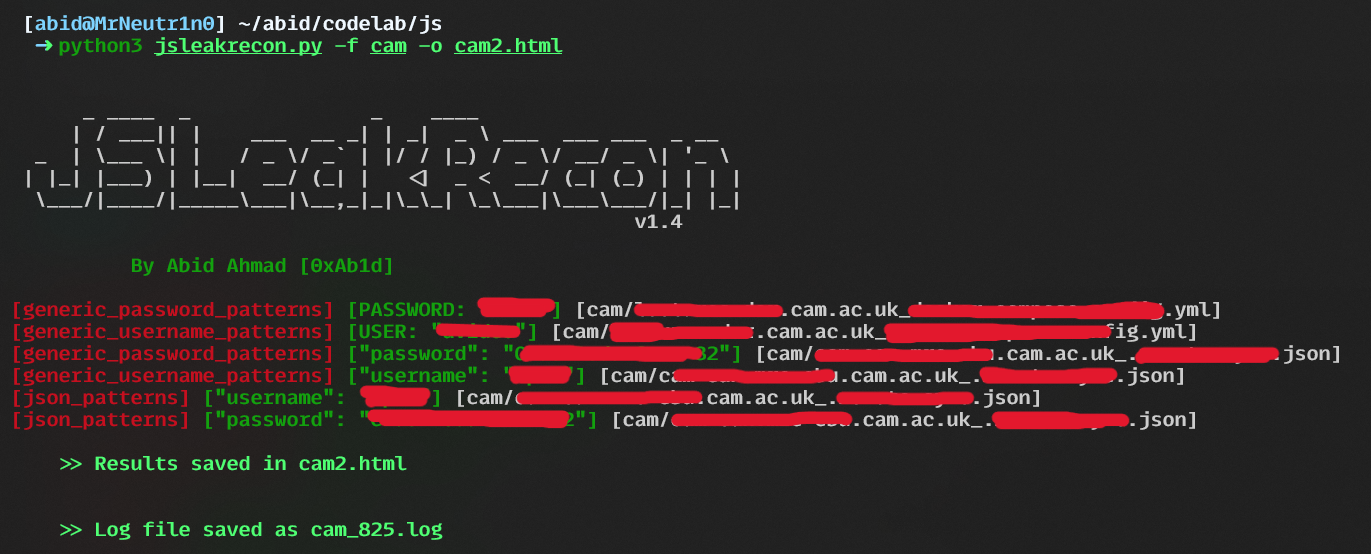
Quickly Identify Hardcoded Credentials, API keys, Access Tokens, Secret keys, and Critical security issues in JavaScript Files
b-ismi-llāhi r-raḥmāni r-raḥīmi — In the name of Allah, The Most Gracious and The Most Merciful.
JavaScript is an integral part of modern web applications, responsible for everything from dynamic content to backend communications. It is essential for web development but also poses security risks when sensitive data is exposed. Hardcoded credentials, API keys, and tokens often find their way into JavaScript files, leaving applications vulnerable. JSLeakRecon is a powerful tool developed specifically for penetration testers, bug hunters, and security professionals to scan JavaScript files for these potential leaks. It offers dynamic, real-time capabilities that go beyond static code analysis, making it an ultimate tool for offensive and defensive security use cases.
Why JSLeakRecon? The Purpose
JSLeakRecon is designed to detect potential leaks rather than definitive credentials. This approach is crucial in offensive security because the reconnaissance phase is all about collecting information and building a profile of the target. By identifying patterns that suggest sensitive information, JSLeakRecon ensures that no potential vulnerability is overlooked. This strategy provides penetration testers with more possibilities for further testing and exploitation.
Why “Potential” Leaks Matter & Valuable
Immediate Critical Sensitive Information Disclosure: While JSLeakRecon is primarily designed to identify potential leaks, it often directly uncovers sensitive information disclosures within minutes. The tool’s ability to detect hardcoded credentials, tokens, and other secrets can reveal critical findings like API token, secret keys, or authentication secrets that provide immediate access or unauthorized privilege escalation.
For instance, during the development and testing of JSLeakRecon, I used the tool to assess the University of Cambridge’s systems. The tool successfully identified multiple sensitive information disclosure vulnerabilities. As a result of these findings, I was honored with a Letter of Appreciation from the University of Cambridge, demonstrating the tool’s power and effectiveness in quickly identifying and validating critical security issues. You can read the full story [here]
- Information Gathering: Even if some results are not immediately exploitable, but each of them can provide crucial insights that guide further testing and exploitation. JSLeakRecon uncovers these potential leaks, ensuring that penetration testers have every possible lead to validate and explore.
- Expanding Attack Vector: Ignoring potential leaks means missing critical entry points or attack vector that could lead to further vulnerabilities. The tool identifies credentials, tokens, and secrets that could be leveraged during attacks. For example, Found `uid` can be used during IDOR testing, Create precise custom wordlist to bypass admin portal, Gather hidden API endpoints, hidden parameters etc.
Core Features of JSLeakRecon
JSLeakRecon offers a wide range of features designed to enhance its capabilities, making it a versatile tool for both offensive and defensive security professionals.
1. Credential Detection and Categorized Pattern Matching
JSLeakRecon focuses on detecting credentials, secrets, and tokens using categorized patterns in its `regex.yaml` file. This file is structured to recognize a variety of sensitive data, including:
- Passwords, email, and usernames
- API keys and auth tokens, secret key
- Encryption keys and session cookies and many more.
The tool identifies these patterns and categorizes them into generic groups such as generic_password_patterns, generic_secret_patterns, and generic_username_patterns. This modular setup allows users to customize or improve the detection patterns as new types of secrets and credentials emerge.
2. Real-Time, Dynamic, and Multithreaded Scanning Capabilities
JSLeakRecon performs real-time scans directly on JavaScript files from live web applications. This capability allows offensive security professionals to:
- Assess dynamically loaded JavaScript files, providing a realistic simulation of how an attacker would interact with the target system.
- Scan multiple files and URLs simultaneously in multithreading, making it efficient for large-scale web application assessments.
3. Local File Scanning for Secure Development and Compliance
In addition to dynamic web-based scanning, JSLeakRecon supports local directory scanning, making it perfect for developers and security teams who want to audit their code before deployment. This feature is particularly useful for:
- CI/CD Integration: Automating scans during the development lifecycle to catch leaks before code reaches production.
- Secure Code Audits: Ensuring compliance by proactively identifying sensitive information in development environments.
4. Bypassing WAFs: User-Agent and Proxy Rotation
JSLeakRecon includes user-agent rotation and proxy support to ensure that scans remain anonymous and undetected. By rotating user-agents, the tool mimics real browsers, reducing the chances of detection by automated security systems.
JSLeakRecon Usage Instructions
To run JSLeakRecon, the user can specify either a list of URLs or a folder containing JavaScript files:
- List of URLs: Use the `-l` flag to provide a file containing a list of URLs.
python3 jsleakrecon.py -l urls.txt
— –
- Directory of JavaScript Files: Use the `-f` flag to specify a directory containing `.js` files.
python3 jsleakrecon.py -f /path/to/js/files
— –
JSLeakRecon automatically determines the optimal number of threads based on the system’s resources, but it can also be customized if needed:
python3 jsleakrecon.py -l urls.txt -t 10 # Runs with 10 threads
— –
To run JSLeakRecon with proxy support:
python3 jsleakrecon.py -l urls.txt --proxy proxylist.txt
— –
Output Flexibility: HTML, TXT, and Log Files
JSLeakRecon’s results are designed to be user-friendly and intuitive, enabling security professionals to quickly navigate through potential findings.
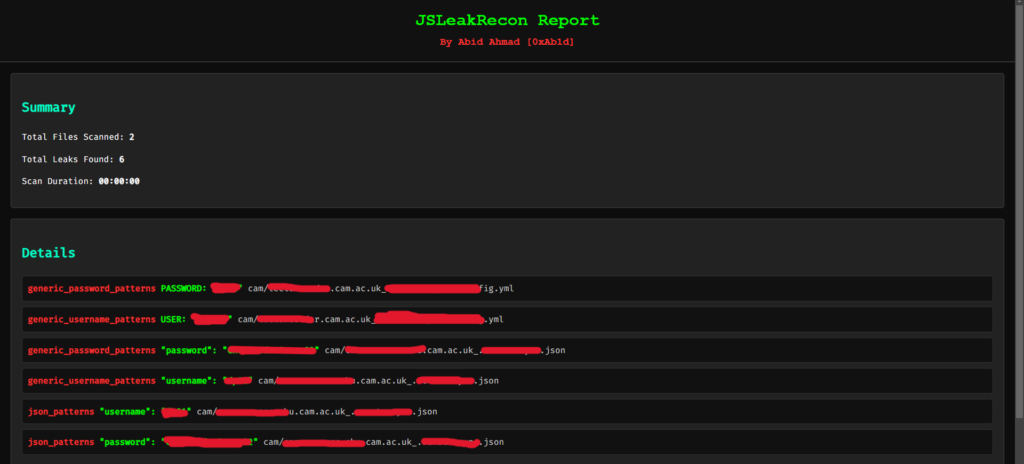
- HTML Reports
JSLeakRecon generates HTML reports that are visually engaging and organized. These reports provide:
- A structured view of detected leaks, making it easy to identify critical findings.
- A format suitable for professional reporting, ensuring that penetration testers can present results to clients or internal teams effectively.
python3 jsleakrecon.py -l urls.txt -o report.html
2. TXT Output
For those who prefer a straightforward and clean output, JSLeakRecon offers TXT reports that filter results into a simple list format.
python3 jsleakrecon.py -l urls.txt -o report.txt
3. Structured Log Files
JSLeakRecon automatically generates log files for each scan, ensuring that all findings are recorded in detail. This is important for:
- Post-scan analysis: Users can revisit logs to validate findings or cross-reference results.
- Documentation: Log files serve as essential records for audits, ensuring that all activities are traceable.
JSLeakRecon is more than just a JavaScript scanning tool; it’s a comprehensive reconnaissance solution designed for both offensive and defensive security professionals. By focusing on potential leaks, the tool ensures that no detail is overlooked, providing penetration testers with valuable insights that can inform and enhance their attack strategies. Whether you are a penetration tester, bug hunter, or security analyst, you can effectively use JSLeakRecon in your operations to explore, analyze, and secure JavaScript files.

