How I was able to find multiple vulnerabilities of a Symfony Web Framework web application
Found high severity vulnerability in 5 minutes just from reconnaissance. Found multiple vulnerabilities on a web application that used the Symfony web framework, enabled Symfony profiler/debug mode.
b-ismi-llāhi r-raḥmāni r-raḥīmi — In the name of Allah, The Most Gracious and The Most Merciful.
Hello! beautiful people,
Today I’ll explain how I found multiple vulnerabilities on a web application that used the Symfony Web Framework where Symfony profiler/debug mode was enabled.
Understanding Symfony Profiler & Debug component
Symfony web framework has a feature called Symfony Profiler. This profiler component can only be used when the debug mode is enabled. Here is the twist. The Symfony web framework is much more secure, but enabling debug mode will make this framework extremely vulnerable. The symfony web profiler component exposes sensitive information of the web application that attackers can abuse.
Then why do developers enable Debug Component?
The Debug component provides tools to ease debugging PHP code. It offers several tools to help debugging PHP code. This component helps developer a lot in the development stage. Symfony provides three environments by default called dev, test, and prod (production). Symfony highly recommends disabling profiler tools in the production environment. But sometimes, developers forget about it and make the web application vulnerable.
How I found vulnerabilities (Step by step)
Let’s assume the target site is https://redacted.com. I have found this vulnerability on a subdomain of the target (https://sub.redacted.com).
Atfirst, I browsed the subdomain and checked what web technologies were used. Using the Wappalyzer addon, I discovered https://sub.redacted.com used the “Symfony” web framework.

Then I proceed to the asset discovery phase. Initially, I tried to fuzz directories using FFUF. I have found an interesting file which is “app_dev.php”. It indicates there might be Debug mode for Symfony is enabled.
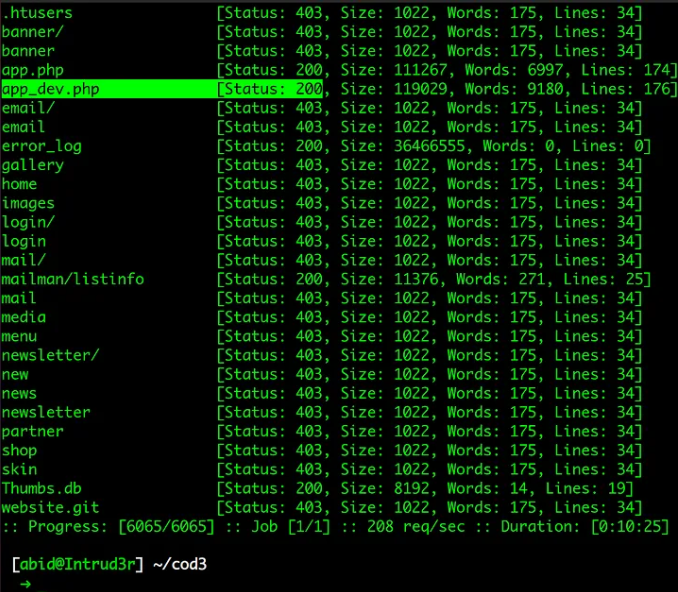
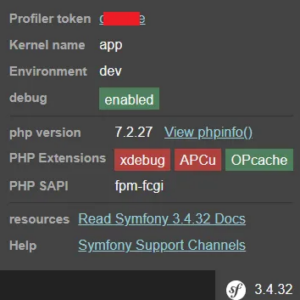
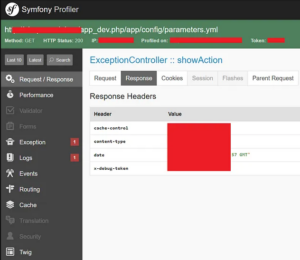
Let’s check it on the browser. Whenever I browsed “https://sub.redacted.com/app_dev.php”, found debug mode is enabled and got a profiler token to access Symfony Profiler. Also, I got the phpinfo file location.
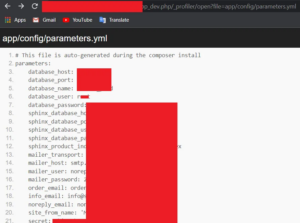
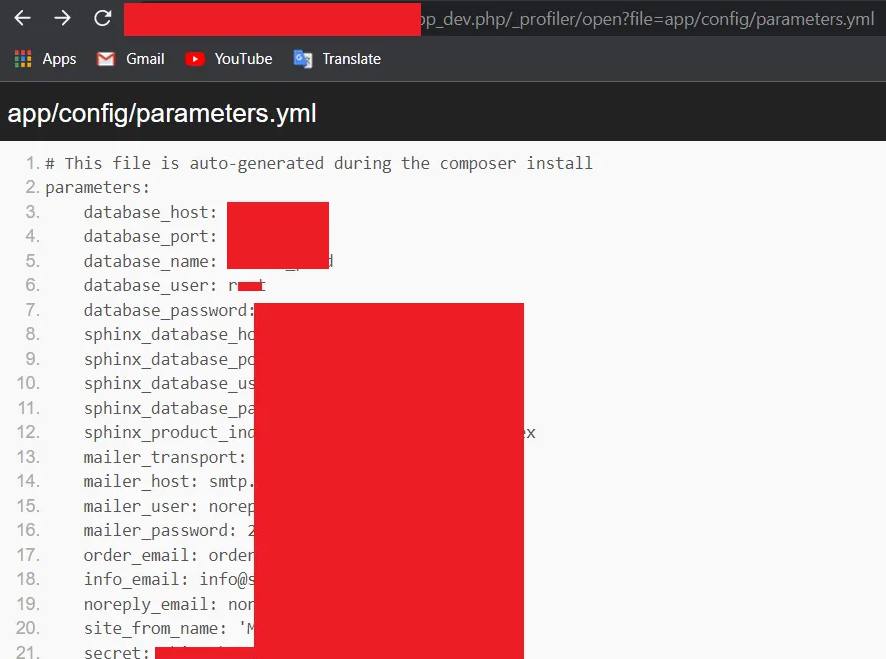
Until now, the severity of my finding is Medium. I knew Symfony Debug toolbars allow reading files that could expose sensitive information. So, I tried to dig more to increase the severity. Then I researched some articles and read Symfony web framework documentation. I found Symfony version 3.4 database default configuration file location, which is app/config/parameters.yml

So I tried to open configuration file and Boom. I have found database and mail server credentials.
Impact
The impact of exposed credentials has a wide range of consequences because those credentials can be used in data breaches, system compromises, loss of brand reputation, as well as financial losses.
Mitigation
Disable the debug mode by setting APP_DEBUG to false. Debug mode should be disabled in the production environment.
Tips: If you found a web application that uses the Symfony web framework, do not forget to check debug mode and profiler. It might be developer forget to disable it.
- https://example.com/_profiler
- https://example.com/app_dev.php/_profiler
- https://example.com/app_dev.php